Artificial intelligence is the latest IT buzzword that everyone seems to focus on and it’s because it is a big deal. Advances in computing have created an environment where developers can create software that effectively learns. Unfortunately, due to the nature of AI regulation; or, the complete lack of it, there are some who are concerned that the technology—which could be a revolutionary tool for the improvement of human societies—is being degraded.
Directive Blogs
Artificial intelligence, or AI, has upended the way that we discuss technology in business, society, and individual everyday life. While we mostly focus on the benefits of the technology, there are many downsides to consider as well. That’s what we’d like to discuss today; how AI has a dark side to it that potentially requires regulation.
In recent years, there has been much debate about how companies collect, sell, and use personal data. Many businesses make extra money by selling data they collect about people. This might seem like a side effect of all the data we create online, but it can lead to some tricky problems. Today, we'll look at something called the "data-broker loophole," how it works, and what we can do about it.
For the longest time, smartphone manufacturers looked to develop devices that came with unique features in all different manners of form factors. Nowadays, however, there are very few phone manufacturers and those that are left have pretty much decided, for now, what the smartphone would look like. Even the ones that fold in half look and function pretty much the same. In this week’s blog, we will take a look at the declining innovation in the smartphone market and why it may not be a bad thing.
You might remember the buzz when Josh Allen, a digital artist, won first place at the 2022 Colorado State Fair for his digital artwork called "Théâtre D'opéra Spatial." The catch? He created the image using AI. Now, he’s in a fight with the Copyright Office to prove that his work deserves copyright protection.
Being a green business is certainly not a bad thing. Not only does it help boost your company's environmental friendliness, but it can often attract customers and clients who prioritize the environment. Less mentioned, however, is how being greener can actually give your business an advantage in the right circumstances.
As technology continues to gain prominence in healthcare, it plays an increasingly vital role. Advancements in technology have allowed the healthcare industry to stabilize costs, improve access, and personalize care delivery—objectives that were challenging in the past. These benefits come with a potential downside: data privacy issues, which are becoming more concerning as technology advances.
Google Search is a cornerstone of the internet, used by billions of people daily to find information quickly and efficiently. But have you ever wondered what happens behind the scenes when you type a query into Google and hit "search"? Let's dive into the intricate process that powers the world's most popular search engine.
Did you watch the big game this year? Chances are that if you did, you got to witness all of the spectacles that the event had to offer, including a lot of technology that enriched the experience, whether you realize it or not. The National Football League has implemented emerging technologies that have helped solve persistent challenges over the years. Let’s explore some of these technologies.
While most of us know that Santa Claus lives at the North Pole, fewer know that he’s specifically built his big, rambling castle in the Laughing Valley. It is there that he and his workforce, the elves, sprites, pixies, and fairies that help him make his toys all live, all working hard to give the children of the world their presents each year.
Of course, as magical as Santa and his team may be, it isn’t unheard of for them to need a little help every once in a while.
We have the pleasure of working with many businesses, some of whom take more advantage of our remote services than others. We wanted to take a few moments to discuss one of our more discreet client organizations and a challenge we helped them resolve. Hopefully, sharing this won’t land us on the naughty list.
What is art? It’s not an easy question to answer, especially with new techniques and mediums being developed all the time. By definition, art can be basically summed up as the creative expression of an individual through some medium.
For Japanese artist Tatsuo Horiuchi, that medium is one that is familiar to those in and out of the art world.
Since its domain was first registered on September 15, 1997, Google has exploded from a relatively simple search engine to the massive assortment of platforms and services that fall under the Alphabet umbrella. That being said, most people tend to think of very specific aspects of Google’s Search function… like the amusing Easter Eggs that the platform has become somewhat famous for.
The use of technology is one of the things that brings most people together. For the past couple of decades people have depended more and more on technology as a way to manage their lives, socialize, and get the goods and services they choose to purchase. This has led to the development of a lot of solid technology-related television shows. In this week’s blog, we thought we would take a look at three shows that cover multiple genres that are solid viewing for the technology enthusiast.
We tend to focus most of our attention on how to maintain your business’ technology over time. This only makes sense—we are a managed service provider, after all—but that being said, your IT is not the only element that needs to be properly taken care of. It is just as important that you and your team members are physically able to focus on work…something a desk job doesn’t always help.
Technology fatigue is the mental grinding that comes with the overwhelming use of technology in our lives. Many people in the workforce haven’t had to use technology as much as they do today and the ever-growing demand for technology in business creates problems for employees (and therefore businesses). This week, we thought we’d discuss the truth behind technology fatigue and how individuals can do a better job of not getting burnt out from tech.
The thing about technology is that, regardless of how miraculous or otherworldly it may seem upon its introduction, it can quickly become so very familiar to us. Hard as it may seem to believe, someday (maybe even soon), things like ChatGPT and other bleeding-edge technologies will seem typical, perhaps even humdrum.
Whether or not you believe acronyms are an acceptable form of speech, some people might use them habitually or instinctively even for business communications. Of course, they don’t have much place in this context, but habits are hard to break. To address this issue, one innovative thinker has created a tool that can help determine if the acronym “LOL” is sincere or not.
Have you ever heard of the Uncanny Valley? It’s the theory that explains why the human race tends to prefer humanoid robots, but only up to a point, after which we find them unsettling. It’s one reason why so many people found the 2019 film Cats bothersome to watch. The Uncanny Valley has also been present in film in recent years, especially when actors who have passed are recreated digitally to make an appearance, or when talent needs to look older or younger than they are.
Who are you? While it’s a question that’s been asked in all contexts with all levels of metaphysicality attached—from asking someone their name to prompting someone to follow a path of spiritual self-discovery—the growth of the metaverse once again urges us to ask it in a more literal way. When accessing a conglomeration of various services and platforms, how many identities will each user need to juggle?
If Edgar Allan Poe worked in an office, here’s what one of his works would sound like:
True!—nervous—very, very dreadfully nervous I have been and am, but why will you say that I am mad? The office had sharpened my senses—not destroyed—not dulled them. Above all was my sense of hearing. I heard all things in heaven and on earth and many things in…the other place. So, how then am I mad, especially when I can so healthily and calmly tell you this story?
It is a legitimate question whether something is actually art if it isn’t created by a human being. That’s before you are exposed to it, however. In fact, an AI created a piece of art that was crowned the winner at the Colorado State Fair. Let’s take a look at AI art in the context of this competition.
While we typically focus on how various technologies can be used in business applications as a way to boost a small or medium-sized organization’s capabilities, we occasionally come across a topic that is just undeniably cool (and that we can bring back around to business concerns, to boot). We recently heard about the development of a flexible new wearable that uses AI to monitor the health of the wearer that we wanted to discuss with you.
There is a microprocessor shortage influencing all kinds of businesses around the globe, and it’s only going to get worse following the Russian invasion of Ukraine. Ukraine produces somewhere between 45 and 54 percent of the world’s semiconductor-grade neon, something which is absolutely crucial to the creation of microchips. The invasion has put a halt to neon-refinement companies Ingas and Cryoin, and as you can imagine, this puts a massive strain on an already struggling supply chain.
While remote work has been a relatively new option for many businesses currently using it in their operations, it has already shown considerable benefits. Having said that, it would be incongruous of us if we didn’t also acknowledge one glaring issue that remote work has helped to foster: a sense of disconnect in many of those making use of it.
One of the best ways to create positive change in your workplace is the act of projecting positive thoughts into it. In other words, we’re talking about ditching the typical doom-and-gloom that comes from the workplace and picturing the worst-case scenarios. We’re not trying to plan for the worst here; we’re trying to envision the best in an effort to make it a reality for your company. Let’s explore this concept by examining technology management.
When you think about the workweek, there’s a good chance that some iteration of the 40-hour week, broken into 9-to-5 shifts on the weekdays is what comes to mind. It’s just the way things are done. However, this may not be a good thing. Let’s consider the origins of our modern work schedule, and how changing it could provide us all with some serious benefits.
If you’re familiar with the combination
Up-Up-Down-Down-Left-Right-Left-Right-B-A-Select-Start, chances are good that you grew up in the 80s. This is because this combination of buttons is the infamous Konami Code, a cheat code that video games (and others, including some websites and software) have continued to reference since it first appeared in 1986.
Let’s examine the Konami Code’s origins, as well as the various ways it has been used since.
For the past year or so, most workers around the world were forced to work remotely in order to adhere to the strict social distancing guidelines imposed by governing bodies. Now that the time has come to return to the office, many workers are finding that their expectations are a bit different than they were previously, forcing business owners to respond.
HIPAA—the Health Insurance Portability and Accountability Act—is a serious concern for all healthcare providers that operate within the United States, and for good reason! Since August 1996, HIPAA has mandated that these healthcare providers comply with various best practices. While HIPAA is relatively familiar to many people for assorted reasons, fewer know about HITRUST (the Health Information Trust Alliance) and how these acronyms ultimately cooperate with one another.
Accessibility to the Internet is a hot topic because, at this point, almost everyone should be afforded Internet access. The fact that some people don’t have access to the Internet puts them at a severe disadvantage. One group that has major problems with accessibility are disabled people. Let’s discuss what can be done about that.
Remote work is often lauded for its various benefits—and don’t get us wrong, there are certainly plenty of them to account for. However, it must also be said that remote work is far from perfect. Take the environmental impacts it can have, for instance. Let’s discuss how working from home can prove better for the environment, while also addressing the serious problems it has contributed to—and, just maybe, how we can help minimize some of them.
For all its benefits, remote conferencing isn’t the easiest means of doing work for many people, as many have found out through experience. With businesses quite literally forced into this approach for some time now, employees are starting to feel the toll. Let’s discuss some of the impacts that long-term remote conferencing has had, and what can be done to minimize them.
In the United States, the political scene is extremely divisive. This can be seen in nearly every political arena including the ongoing debate over who should have regulatory power over the Internet. In 2017, the Federal Communications Commission voted, three votes to two, to repeal the Net Neutrality rules that were implemented by the same regulatory body just two years prior. Today, with a new administration being sworn in in less than a month, we thought we’d revisit the net neutrality rules and see where we stand at present.
The strangest year in our lives is coming to a close and the holidays figure to be just as strange. With the COVID-19 pandemic still roaring away, there probably won’t be a lot of the events that are typical this time of year. That doesn’t have to ruin the time of year, however. Today, we thought that we would take a look at five cool tech gadgets and services that won’t break the bank, but will also be a cool addition under the tree or for your secret santa.
The United States of America is well into its 2020 election season. Social media platforms, and other online services, are taking notice. Given the misuse of social media and other platforms in past contests, there is little wonder that there is some very real pressure on these platforms to establish policy and security measures to prevent these behaviors this time around.
Here, we’ll take a neutral look at the situation, and explain the initiatives that online platforms are now enacting.
In a rare turn of events, Google and Apple have teamed up with local governments to help slow the ongoing spread of COVID-19. How would you like an app that could notify you if someone you had been in proximity to had tested positive for COVID-19? As useful as this collaboration could be to staunching the pandemic, many people are in uproar about it, and have begun to spread misinformation.
With COVID-19 urging people to remain at home, many telecommunications companies have started to make concessions to make life easier for their customers. Whether it is used for entertainment, work, or communication, Internet access is crucial right now, and so ISPs and cell carriers are taking steps to help facilitate this.
Parker sat at his desk looking at a business card. He watched the snow fall lightly outside his window. He was the last person left in the office, as he typically was this time of year. He put down the business card and got up and walked over to the large pane of glass that was the only insulation from the harsh, cold wintery night. He placed his hand on the window and felt the bitter cold meet the palm of his hand. He stood there for a minute; maybe more than a minute. He began to cry. He was so angry at how things were going.
Cybersecurity is becoming a massive issue for every organization due to the immense amount of data breaches that take place regularly. Businesses of all types are looking at strategies to protect their sensitive customer and employee data from hackers, malware, and any other potential danger. The problem is it’s not always as simple as just implementing cybersecurity software.
Social media - we can’t live with it, but we really can’t seem to live without it. People who frequently read our blog will notice how often we discuss Facebook, one of the biggest players in the social media space. Seeing as privacy is one of the biggest concerns today, we’re wrapping up our short series on Facebook by reviewing the settings you might not have realized were options on your Facebook profile.
When we write about Net Neutrality, we typically write about how it is designed to keep the telecommunications conglomerates, who make Internet service available to individuals on the Internet, honest when laying out their Internet service sales strategy. One way to put it is that without net neutrality in place, the Big Four (which are currently Comcast, Charter, Verizon, and AT&T) have complete control over the amount of Internet their customers can access.
There has been a lot made in the media about the effect that movies and television has had on society. More often than not, the media that is produced is a result of the ebbs and flows that happen in society, which ironically makes the whole notion that television and movies affect society an interesting paradox. The ludicrous portrayal of criminality in media is one issue that is resoundingly debated by lawmakers and sociologists, alike.
The IT guy, Jacob left last month: to begin with. There is no doubt whatever about that. He left without an exit interview, and he didn’t seem very pleased with the way the situation played out. You could never tell if Scrooge cared or not. His demands have never wavered. He expected perfection and when mistakes were made, they were approached as catastrophic affronts to the sustainability of the business, even if that wasn’t the reality.
Recently we’ve seen figures, public and private, lose their jobs and sometimes even their careers over things they’ve posted not only in the present but the past on social media. While public figures may have the resources to put up a fight, those in the private arena often don’t, and so the double-edged sword of attention can be particularly sharp. Once average people attract the all-seeing eye, never forgetting and unforgiving memory of the Internet, they find the weight of public opinion brought down upon them; with all the consequences - positive and negative - such attention may bring.
Children are the future, as the saying goes, so do we really want the future to be taught using tools from the past? While some schools are still using technology that better belongs in the 20th century, others are embracing innovation and teaching in ways that better translate to the “real world.” Let’s take a look at how our evolving technology is transforming the classroom and explore some ways to get it to more students.
With information technology touching nearly every part of modern culture, it isn’t a surprise that it is being utilized by sectors of industry where you may not expect. One of those sectors that may not register as one of the most IT-centric is the criminal justice system. This is largely because it is traditionally thought to be filled with jobs that seemingly haven’t changed much in centuries. Today, we’ll take a look at the technology that fuels today’s criminal justice system and see how municipalities and companies, alike, are benefiting from technology solutions.
Police
To start the journey through the legal system, we’ll start with the people whose job is defined by exercising moral authority: the police. The first thing that anyone needs to know about their investment in IT and their use of technology systems is that, since the police gets a majority of their funding from public money, IT budgets aren’t always in line with a private business’. In fact, some police departments don’t see the point in more IT when good cops are being laid off so they will deliberately cut their IT budgets in line with the budget they get from their municipality.
While IT isn’t always a priority for the police, it can be effective at providing exceptional departmental productivity gains. With the remote nature of the job, most police cars today are outfitted with laptops and Internet accessibility. This allows officers to access motor vehicle and individual information stored on useful databases, but since these machines are hardwired into a car dock, they only get a partial benefit of mobility. Innovative solutions are now being used where police are outfitted with department-owned smartphones and tablets so that officers can access relevant information from outside of their cars.
There are several parts of the job where police can benefit from new technology. Along with the in-car computer networking, and potentially mobile device networking, IT can compliment a lot of what a police officer does. The right IT solution can boost communication, augment (or completely run) operational capabilities, and effectively reduce costs by providing information faster and speeding up procedure. After all, a large percentage of effective policing has to do with having actionable information. As a result, by implementing IT solutions, the public welfare improves--which is the situation that any citizen can ask from their officers of the peace.
From a software perspective, here are three types the typical police department can’t do without:
- Computer Aided Dispatch (CAD) - An application that assists dispatchers route police resources to places of priority need.
- Geographic Information System (GIS) - An application that provides in-depth geographic information to provide dispatchers and officers a comprehensive view of the landscape.
- Records Management System (RMS) - An application that provides officers with access to reliable information to assist them in their duties.
Lawyers
Moving on to the lawyers, we’ll find a professional that is torn between the past and the future. Many lawyers understand that IT can benefit them, but at the same time the simply don’t have time to monkey with technology that, for some, can do more harm than good. The average lawyer that works criminal cases, whether they are prosecutors, defense attorneys, or specialists, understands how to effectively utilize certain technologies to provide their clients the best service possible. After all, they deal with a lot of sensitive information, and have a responsibility to protect it.
Some of the technologies that law firms typically utilize come in the form of business-type solutions that enhance their productivity, efficiency, and data redundancy. Others, however, are best utilized by a business like a law practice. Most practices need strong collaborative systems that allow multiple people to share files, the ability to print off documents, and a central database that has access to documents. These requirements make computing solutions in the cloud a perfect fit for the modern law office. Cloud computing can offer these organizations a way to host all their necessary software, while also providing virtual hardware and redundant storage capabilities without having to pay huge upfront costs.
Lawyers typically use the following software:
- Practice Management - An application that is designed to help lawyers and their staff manage the large quantity of work they are inundated with.
- eDiscovery - An application that makes finding, collection, identifying, and sharing relevant information easy.
- Video Conferencing - Lawyers are extraordinarily busy and often don’t have time for face-to-face meetings. Video conferencing helps fill the void by allowing them to meet with clients, colleagues, and staff from anywhere with an Internet connection.
The Court
Since its main purpose is to be a place to hear arguments, the courtroom doesn’t need all the technology that the police and lawyers use to keep things rolling efficiently along. In fact, most of the technology that is utilized in the duration of a criminal trial would be traditionally provided by the prosecution or defense. This simply isn’t so today. The courtroom of the information age is seeing a major shift, and changing the nature of litigation completely.
The biggest change to the modern courtroom is in the availability of data. Since data is now able to be securely broadcast from cloud servers to devices such as laptops and tablets, the notoriously slow court proceedings’ pace has quickened somewhat. Other technologies like wireless Internet connections and charging ports add to the connected courtroom effectiveness.
Along with the technology people bring in to the courtroom, there are major changes in the technology inside the courtroom itself, too. The modern courtroom features video displays--either in the form of a mounted screen and a LCD projector or smaller, individual screens in the jury box--to provide juries a resource to see evidence. Many courtrooms also have individual witness monitors and annotation monitors.
Since the courtroom only has a couple of static employees, software isn’t typically necessary to manage the staff or used for productivity, but some software is available. There are titles for court and case management, e-filing, and audio-visual that are all found in the modern courtroom.
Corrections
The criminal justice system ends with institutional corrections (prisons and jails) and community corrections (probation and parole). Like the other parts of the system, the corrections system has become dependant on the use of technology, especially for communication. Internet-based databases help corrections professionals track and maintain records on offender rehabilitation, while also helping provide an alternative to incarceration for nonviolent offenders. This provides the public significant cost savings, while also providing correction officers the ability to effectively monitor and manage offender probation.
Since budgetary considerations can really put a damper on the amount of acceptable innovation in corrections, the use of standard information technology is extremely important. It is making prisons and jails safer, and community corrections more effective. No better example of this than then the use of asset tracking technology through an automated offender management system.
The automated offender management system allows multiple users to access (and alter) an offender’s record simultaneously.with other users. This real-time information sharing improves efficiency, as the more information that’s available between multiple elements of the criminal justice system (and in this case, the corrections system) the better the entire system moves. Additionally, by providing real-time inmate information to corrections officers, it will reduce security risks.
If the technologically puerile criminal justice system is utilizing technology to improve operations, your business can, too. To see how Directive’s knowledgeable IT consultants can make technology work for your organization, call us today at 607.433.2200.
As technology has evolved, so have our capabilities of using it. While this has led to great improvements in how we can live our lives, it has also made it much easier for us to torment and harass one another. This is a huge problem, and growing, so it is important to know how to take a stand against it - both at home, and in the workplace.
The office is a workplace, so it most likely isn’t a place that is often associated with fun and games. However, different aspects of games have been shown to provide significant benefits when introduced into the professional environment. Today, we’ll explore some of the ways that a little frivolity may benefit your office.
The Internet of Things has been growing rapidly, and with this growth it has become a major part of daily life. There are connected devices you couldn’t even fathom being needed, but some have turned out to be exceeding useful. In 1977, the release of Star Wars saw people’s imaginations expand. The science end of the sci-fi went into overdrive, and soon communications and computing would change forever. Despite being a long time ago in a galaxy far, far away, the Star Wars universe introduced several concepts of the Internet of Things, decades before the IoT was even conceptualized. This week, we will take a look at the modern day Internet of Things, and how Star Wars primed us for our own future.
Star Wars is a cultural phenomenon. For the past 40+ years audiences from all around the world have become enthralled with the characters, the story, and the technology that existed a long time ago in a galaxy far, far away. Who knew that it was also a wonderful lesson in modern IT security? For today’s blog, we look at three situations that happened in Star Wars: A New Hope; and, how, if proper IT strategies were put in place, the Empire would have been able to protect its greatest asset.
On March 23rd, 2018, the United States Congress passed another spending bill that could potentially limit individual privacy protection all over the world. This bill included a provision called the Clarifying Lawful Overseas Use of Data (or CLOUD) Act, which makes changes to the Stored Communications Act of 1986 and provides unelected American officials a considerable amount of power over digital privacy rights.
In today’s political, social, and economic environment, information is more valuable than ever. However, this increased importance, paired with the speed that data can be dispersed via the Internet, has enabled many to use false information to manipulate the general public into agreeing with their views and acting upon them.
 The holidays are getting closer, and picking the right gift for someone is only becoming a more stressful activity. To make things a little easier for you, we’ve found some gadgets that might make the perfect gift for that person on your list who has a particular interest. This blog will go over some of these interests and the gifts that might make their holiday.
The holidays are getting closer, and picking the right gift for someone is only becoming a more stressful activity. To make things a little easier for you, we’ve found some gadgets that might make the perfect gift for that person on your list who has a particular interest. This blog will go over some of these interests and the gifts that might make their holiday.
For the last several years, we have annually asked the members of our team what they were grateful for. It doesn’t have to be a major thing, just some way that technology has improved our everyday lives. After a few silly answers, like memory foam (which is great) and forks (also important technology), they ended up coming up a few great technologies that they are thankful for. Here’s a few stand out items that we wanted to highlight:
Many consider the beginning of the holiday (shopping) season to be Black Friday, the day after Thanksgiving. This day is infamous for deals so good, people are willing to wait in line for hours before the stores even open in order to take advantage of them--however, are these deals really the best, when Cyber Monday is now in play? We examined what can be expected on the major deal days to find out.
When it’s time to replace your technology, it might bring about a sense of panic. How can you replace your technology without breaking your budget, or worse, exposing data on your old technology to potentially threatening actors? Only one thing is for sure; you need to make sure that you have a solid strategy to adhere to when you need to replace your broken-down technology.
Did you know that over 2,000 Domino’s Pizza franchises in Australia, New Zealand, France, Belgium, The Netherlands, Japan, and Germany feature delivery by robot? Starship Technologies, a self-driving robotics company, announced on March 29th that they would be partnering with Domino’s to revolutionize the way the delivery process works.
In October of 2016, the Federal Communications Commission designed a set of rules known as the Broadband Consumer Privacy Proposal. These rules had intended to flip the status quo and require Internet service providers (ISPs) to gain their customers’ permission before they harvested their browsing histories to sell to advertisers. This proposal is now moot with the establishment of a new law that passed through Congress and was signed by President Trump in April 2017.
 In November of 2016, Governor of New York Andrew Cuomo devoted $30 million dollars to a 50-mile-long flight traffic management system to promote the use of unmanned aircraft systems (more commonly known as drones) for Central New York business purposes. This ‘corridor,’ as it is called, will stretch from Griffiss Air Force Base in Rome to Syracuse by sometime in 2018.
In November of 2016, Governor of New York Andrew Cuomo devoted $30 million dollars to a 50-mile-long flight traffic management system to promote the use of unmanned aircraft systems (more commonly known as drones) for Central New York business purposes. This ‘corridor,’ as it is called, will stretch from Griffiss Air Force Base in Rome to Syracuse by sometime in 2018.
 There are an unfortunate number of cyber threats out there; protecting your company’s network from these threats is paramount. In order to find out how acquainted you are with the malicious programs and attacks that could harm your business, we’ve devised this quick quiz to test your knowledge.
There are an unfortunate number of cyber threats out there; protecting your company’s network from these threats is paramount. In order to find out how acquainted you are with the malicious programs and attacks that could harm your business, we’ve devised this quick quiz to test your knowledge.
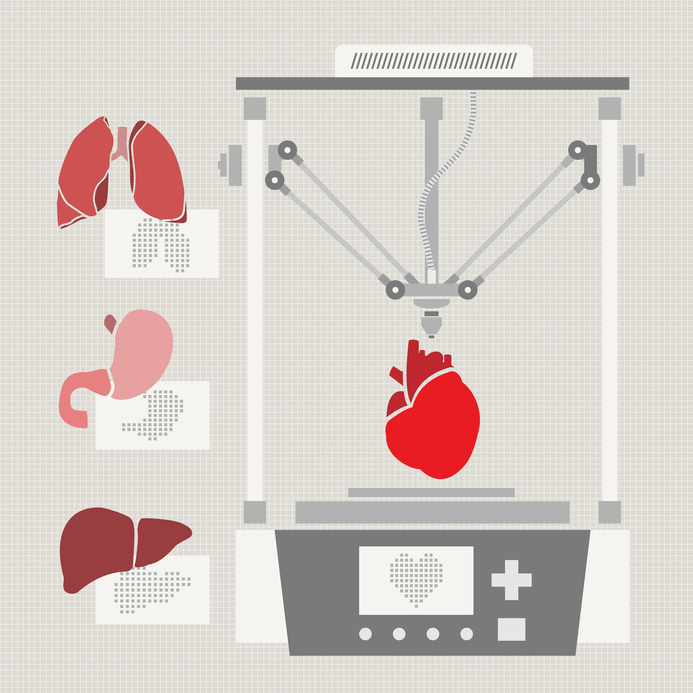 The concept of 3D printing is becoming a factor in more and more industries, perhaps most promisingly in the healthcare sector. This specialization has the potential to revolutionize how patients are treated for some very serious maladies, as well as how well they adjust to their life during the post-treatment stages. However, this application of 3D printing is not without its concerns.
The concept of 3D printing is becoming a factor in more and more industries, perhaps most promisingly in the healthcare sector. This specialization has the potential to revolutionize how patients are treated for some very serious maladies, as well as how well they adjust to their life during the post-treatment stages. However, this application of 3D printing is not without its concerns.
Let’s say you’ve got an email that you really need to crank out from home, and pronto. So, you whip out your laptop to get started, and that’s when you spot the menacing eyes of a toddler from across the room. What do you do? Is it even possible to use a mobile device once a toddler has it in their greedy little sights? For this week’s tip, we’ll explore your options.
The Internet of Things may have just entered social consciousness, but people have been trying to add Internet functionality to devices for quite some time. One instance of this is the development and manufacture of smart car technology. In the same way as our services are designed to proactively monitor and maintain your business’ network, a smart car has been developed largely as an completely connected automobile that allows car owners to worry less about their car and to get the most out of their investment and driving experiences.
One of the most high-profile hacking attacks in the United States struck last year when the Internal Revenue Service (IRS) was breached. 464,000 Social Security numbers were swiped; enough to file 101,000 tax returns using false personal identification numbers. Every organization can learn how to better protect themselves during tax return season, especially since you have so much on the line every year.
Let’s say that you're on a business trip. As you travel, you decide you may as well get a bit of work done. You pull out your laptop and are pecking away, and that’s when you notice a growing feeling of nausea rising in your stomach. It gets so bad that you finally have to put the laptop away, having accomplished relatively little, before you are sick.
Ransomware is a dangerous malware that all businesses fear. Although, if the right precautions are taken, a ransomware attack can be completely thwarted. A recent hack attack of the San Francisco Municipal Transportation Agency provides us with a real-world example of this, which helps make ransomware appear a lot less formidable.
In a historically large media merge, AT&T and Time Warner have come to an agreement in a proposal that has been discussed since as early as August 2016. The wireless provider intends to purchase Time Warner’s media holdings for a whopping total of $85.4 billion in cash and stocks, assuming the merger passes the inspection of antitrust regulators.
It can be easy to underestimate the importance of maintaining permissions on your network. In fact, sometimes it takes a good dose of misfortune to present the consequences of unchecked access to your network. This time, the misfortune befell PA Online, an Internet service provider located in Pennsylvania.
It’s safe to say that hacking is a frowned-upon practice, but that hasn’t stopped cyber criminals from attempting to turn a profit off of it. This practice has led them to target nonconventional organizations, including hospitals and other healthcare facilities. However, just because a hacker can target a hospital, does this mean that they should? This is a topic of some debate amongst hackers, whom, believe it or not, actually do have some sort of ethical standards.
The busy business owner rarely has time to indulge in extracurricular activities, but there are still ways that you can make progress--even when you’re not actually in the office or working on important plans, there’s still the opportunity for self-improvement. One way that you can do this is by being well-read. In fact, science has practically proven that reading literary fiction is just as beneficial for your professional development as other seemingly more practical works.
A business owner is always looking to improve their skills and learn about new ones. It’s natural to want to learn new things, even if you’re already an expert in your own field. The 10,000 hour rule offers a few guidelines to help you learn a new craft, but it’s not as easy as consistent practice. You might be in for a long journey toward “expert status.”
There’s no question about it; hackers make things difficult for businesses of all industries and sizes. They go out of their way to steal data and turn a profit off of it, as well as misrepresent organizations and individuals. The business environment is chaotic enough without hackers mucking everything up. However, the recent hacking attacks behind the group Anonymous have evolved the persona of the typical hacker into something very different.
Having a workflow that works for you is the key to being successful. Sometimes, finding such a routine requires taking some rather extraordinary measures. If you’re looking for ways to tweak your workflow to be more productive, then consider these outside-the-box productivity tips from some of history’s very successful people.
Memes are deeply rooted into today’s online culture. Thanks to the Internet, even the most absurd things can quickly gain popularity through social media and online forums. While they might seem silly and pointless, it would be foolish to dismiss them as wastes of time; especially considering how popular they are. If you are looking for a creative way to get your name and brand out there, why not try using memes?
Do you loan out your Netflix password to friends so that they can catch up on their favorite shows? If so, you’re in violation of a recent federal court ruling, which declares that sharing a password of any kind is now a federal offense. So, if you plan on watching the new Netflix original series Stranger Things, you may want to reconsider how you plan to do so.
Cyber security professionals and Internet users rejoice, for the “Spam King,” Sanford Wallace, has finally been sentenced for his longtime use of stolen Facebook credentials to spam other users. Between 2008 and 2009, he had stolen credentials for Facebook accounts, and then used the accounts to send credential-stealing web links. Now, he gets to spend the next two and a half years in prison, and pay an oddly-specific fine of $310,629.
When you think of a computer, you think of a machine that makes your life easier. You can look up events, check facts, record data, and so much more. However, the first computer might be something extraordinarily unexpected; a submerged treasure off the coast of Greece called the Antikythera mechanism, which was used to predict and track astronomical events, like the movement of the planets or the occurrence of eclipses.
Upgrading technology is a sure way to improve the efficiency, security, and productivity of your company’s operations, but is there a point when upgrading one’s tech can go too far? As much as you hear us sing the praises of upgrading, we have to admit that there’s a point when you can have too much of a good thing.
 When you think about the stock market, one vibrant image that comes to mind is the chaotic trading floor of the New York Stock Exchange, with traders climbing over each other and barking orders. Today, the NYSE trading floor is much more subdued, a testimony to just how much technology has changed the financial marketplace.
When you think about the stock market, one vibrant image that comes to mind is the chaotic trading floor of the New York Stock Exchange, with traders climbing over each other and barking orders. Today, the NYSE trading floor is much more subdued, a testimony to just how much technology has changed the financial marketplace.
 In a recent poll by WSJ/NBC comparing tech companies to US presidential candidates, Google came out on top with 67 percent of respondents having a positive opinion of the company. Compare this to Apple’s 54 percent, and 43 percent going to the highest-rated candidate. Perhaps Apple and the politicians can take a cue from Google and make use of Easter eggs, because who doesn’t love Easter eggs?
In a recent poll by WSJ/NBC comparing tech companies to US presidential candidates, Google came out on top with 67 percent of respondents having a positive opinion of the company. Compare this to Apple’s 54 percent, and 43 percent going to the highest-rated candidate. Perhaps Apple and the politicians can take a cue from Google and make use of Easter eggs, because who doesn’t love Easter eggs?



